Principles of Information Security
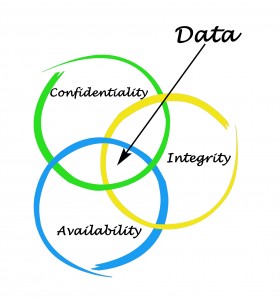
The principles of Information security (IS) are the preservation of confidentiality, integrity and availability of information, known as CIA. This is not just about client data, despite the tendency to focus on this.
Other elements that could be equally critical will include staff data, corporate information, such as financial, product specifications, supply chain data, and any other information that is essential for the running of the organisation.
Principles of Information Security
- Confidentiality – ensuring the privacy of information, ensuring that ‘information is not made available or disclosed to unauthorised individuals, entities’;
- Integrity – ensuring that information cannot be amended or incorrectly deleted, and maintains ‘accuracy and completeness’; and
- Availability – ensuring that information is where you want it when you want it, and is ‘accessible and usable upon demand by an authorised entity’.
Why do Information Security?
You have probably heard of cyber security in the news, and will already have implemented a number of security practices which will be second nature to you; locked doors, passwords, secret PIN numbers, and other such techniques, and may be wondering why you would need to implement an IS process.
However, the implementation of an effective Information Security Management System (ISMS) will help you to understand the nature of the data and information that you hold, and the vulnerabilities of that data.
By properly understanding the risks, you will be able to implement effective risk treatment and control, and will be able to monitor the effectiveness of the protective steps that you have taken.
Additionally, you will be able to have a better understanding of the legislative and regulatory regime for you and your key stakeholders, knowing what all parties require for the confidentiality, integrity and availability of their information.
There are additional benefits to adopting a comprehensive ISMS, which may include:
- Greater confidence for clients and other interested parties;
- Improved data retention and disposal procedures, resulting in reduced requirements for back-up and archiving;
- Improved responses to security events and incidents; and
- Competitive advantage over similar organisations.
Implementation
Implementation of effective IS within an organisation may require a change in the culture, with a change in perception that “everything is generally permitted unless expressly forbidden” instead of “everything is generally forbidden unless expressly permitted”.
However, this has to be balanced against information requirements for innovation and productivity.
Demonstrating Information Security
The implementation of an effective ISMS can be demonstrated through certification to ISO 27001:2022 – Information security, cybersecurity and privacy protection — Information security management systems — Requirements.
Further information supporting the requirements specification can be found in the ISO 27000 series, particularly ISO 27002 and ISO 27005.
We are happy to answer any questions about Business Continuity, Crisis Management, Information Security, Data Protection and Product Recalls.
How Can Cambridge Risk Solutions Help?
Cambridge Risk Solutions provides a range of services to assist with the implementation of Information Security, and have an experienced ISO 27001 Lead Auditor who can assist with readiness for certification to ISO 27001:2022
View some case studies of recent Information Security and ISO 27001 projects.
